The growth of remote work has shattered on-premise models for IT security. That’s why the Zero Trust framework, which evolved more than a decade ago, has recently emerged as the place for security to start.
Zero Trust shifts “trust but verify” to a more integrated and automated approach. This approach replaces internal silos with collaboration, dynamic orchestration and user-centric automation that starts from zero and builds a cohesive chain of trust.
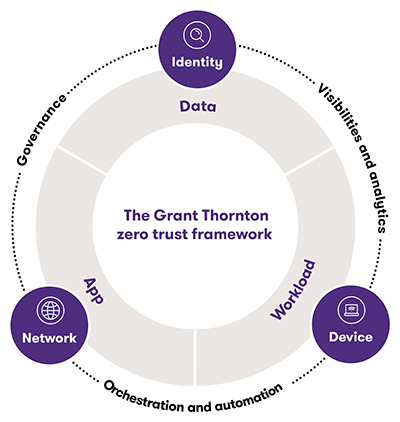
Many organizations have begun to implement a Zero Trust framework. However, the framework includes identity and access management, multifactor authentication, security orchestration, security automation and more. Plus, most organizations need to apply the framework across a complex tangle of identities, devices, networks, applications, apps, cloud infrastructure and workloads across their ecosystems. That’s why organizations have often implemented Zero Trust in some places, but have left other holes of exposure.
To eliminate exposure, you need to expand the Zero Trust framework into a customized architecture to protect your enterprise.
Zero Trust architecture
A Zero Trust architecture is an enterprise cybersecurity architecture based on the Zero Trust principles. It’s designed to prevent several threats and limit internal lateral movement. The U.S. National Institute of Standards and Technology has issued important framework guidance in its NIST Zero Trust Architecture Special Publication (SP) 800-207.
However, an architecture must be tailored to fit the enterprise it protects. The following architecture provides a foundation, but it would need to be extended to protect an Internet of Things (IoT) or Operational Technology (OT) environment:
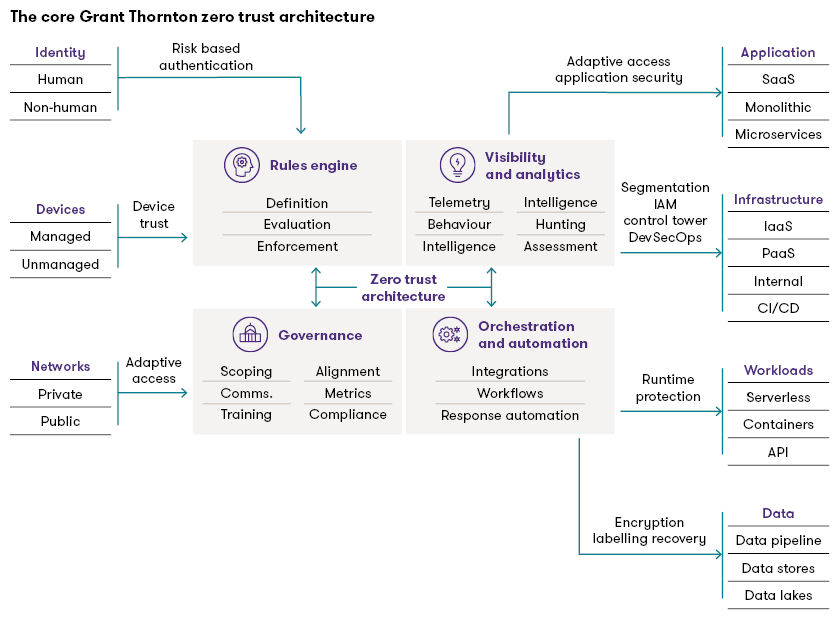
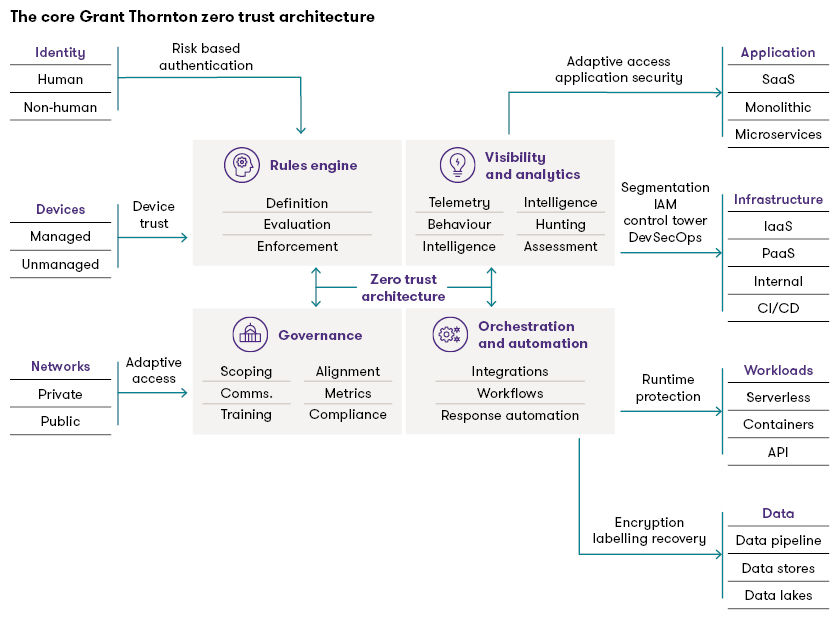
When organizations start to customize and maintain a Zero Trust architecture, many struggle to determine where to start and what capabilities they will need.
Zero Trust starting point and capabilities
Every organization’s Zero Trust architecture will be unique, so the organization’s starting point and capabilities will need to be unique as well. The following sample shows one starting point with some of the capabilities that are often required:
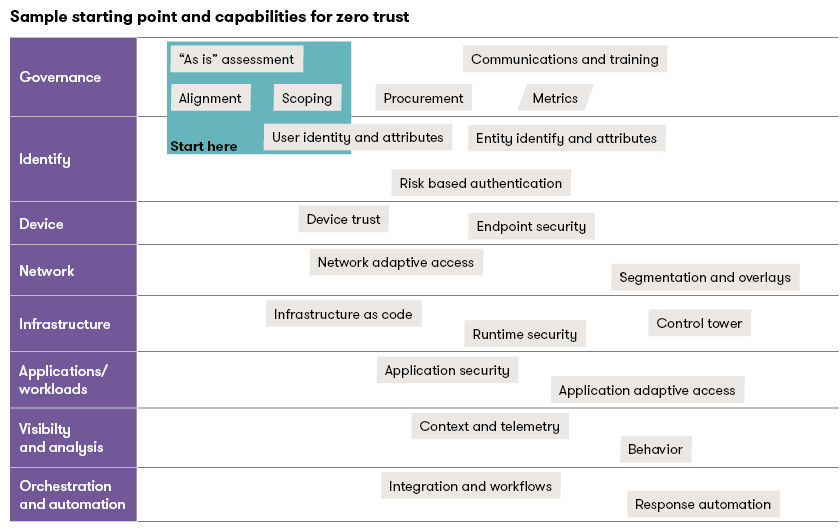
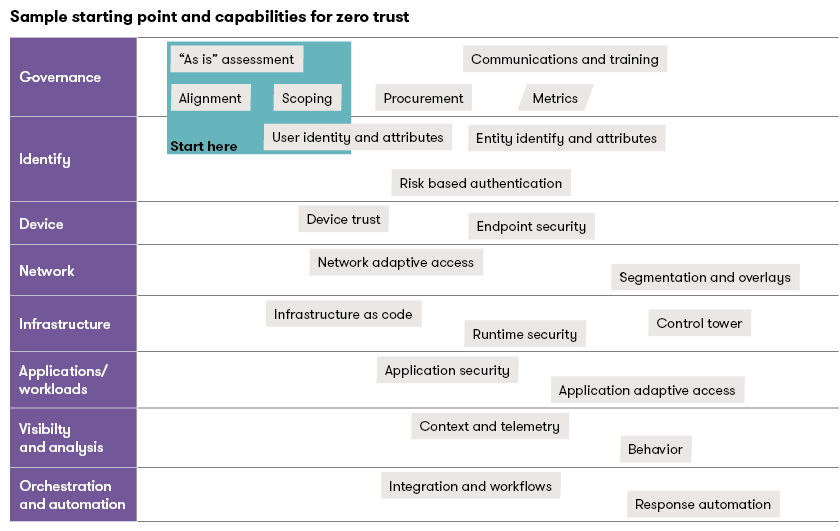
As you begin your journey to implement Zero Trust across your enterprise, it’s important to acknowledge some common pitfalls.
Zero Trust pitfalls
The journey to Zero Trust is both complex and essential — your security is at stake. Here are some of the pitfalls that organizations encounter on the way:
- 1. Trying to do too much at once
Don’t boil the ocean with too many products. Organizations can stumble into this pitfall by taking recommendations from too many vendors or others without a plan, a detailed roadmap and business alignment. Before adopting Zero Trust, it is vital to perform an “as-is” assessment of the environment to understand your starting point, the critical flows and vulnerabilities. - 2. Retrofitting legacy security concepts and models
This problem occurs when organizations try to apply a new name to an old model of perimeters and zone-based protection. The outdated “castle-and-moat approach” assumes that everything outside the “castle” is a potential threat until proven otherwise (still true), and that everything inside can be trusted (now false). This is an assumption you can shatter with a quick search on insider risk or ransomware attacks. The Zero Trust strategy does not apply this static level of trust. Instead, it relies on building a chain of trust, which remains engaged in making dynamic decisions based on the context of actions performed.
“Organizations that use regulatory compliance as their primary driver are experiencing many more hurdles and difficulties in lifting Zero Trust off the ground. Security leaders who built strong alignment with business goals and digital transformation have experienced better collaboration and long-term commitment.”
- 3. Failing to align with digital transformation
Organizations experience more success with Zero Trust enablement when they show strong alignment to their business mission and goals. Leaders experience better enablement and resourcing when they convey the value proposition of the Zero Trust framework beyond simply “good security risk management practices.” A strong value proposition also helps drive success for security functions that are enablers of the organization’s digital transformation strategy. “Organizations that use regulatory compliance as their primary driver are experiencing many more hurdles and difficulties in lifting Zero Trust off the ground. Security leaders that gained strong alignment with business goals and digital transformation have experienced better response and long-term commitment,” said Grant Thornton Risk Advisory Director Jitendra Joshi.
- 4. Neglecting the user experience
Zero Trust is more successful when it is user-friendly. Zero Trust should not burden users with multiple pop-up windows or require them to jump through multiple hoops to log into a resource. Without the right-sized security measures and an excellent user experience, users might be tempted to find workarounds that expose the organization to risk.
- 5. Assembling Zero Trust one piece at a time
This is a big pitfall, if not the biggest. Many solutions address distinct aspects of Zero Trust — like identity and access management, multifactor authentication or security orchestration. But your security implementation can be hampered if you implement these specialized tools without considering how they interact within your existing security and management solutions ecosystem.
A piecemeal approach does not give security teams visibility across Zero Trust, nor does it allow them to take advantage of the collaborative functionality of those tools. A piecemeal approach can also contribute to poor user experience, while introducing unnecessary complexity and cost.
- 6. Underestimating the data effort
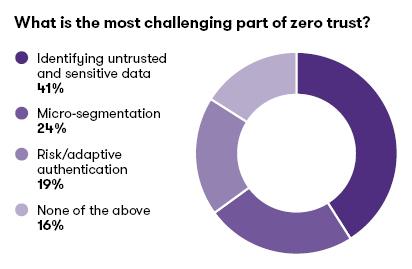
As you plan resources, make sure you are clear about the work required to evaluate data and identify risks. We recently asked security practitioners about the most challenging part of implementing Zero Trust, and their top response was “Identifying untrusted and sensitive data.” The exercise to identify sensitive data could easily overwhelm many security and data teams and lead to pitfall #1 (trying to do too much at once). Organizations should use a phased approach for Zero Trust, with strict controls over scope creep and alignment with business objectives.
- 7. Getting boxed in with one vendor
This pitfall stems from the perception of Zero Trust as a product. With the extensive competition for cybersecurity market share, some of the hype is reasonable. However, combined with all the Fear, Uncertainty, and Doubt tactics in the market, some vendors have led people to believe that they have a “Zero Trust product.” Unfortunately, you cannot buy Zero Trust in a box.
- 8. Buying silos and shelfware
A successful Zero Trust framework requires weaving and orchestrating various security capabilities from multiple vendors. Many technological platforms have various capabilities, so it is crucial to assemble the right solution while minimizing feature overlap and redundancy between components. This problem worsens when companies make buying decisions in silos, rather than adopting an integrated end-to-end strategy.
- 9. Losing commitment over time
Another often-overlooked pitfall is the lack of support for ongoing administration. Zero Trust relies on a carefully and deliberately developed chain of trust. However, people move into new roles and change locations. It can seem burdensome to change their access permissions every time, to ensure that they have the access required to perform their responsibilities. Keeping the orchestration accurate and up to date requires ongoing commitment and partnership across the organization.
To successfully move to a Zero Trust architecture, you must have the right architecture, the required capabilities and an integrated approach to implementing security controls and technology. Invest time to understand and align with the internal transformation roadmap and architecture. Accelerate the adoption of collaborative automation using cloud infrastructure and DevSecOps frameworks.
Zero Trust is not a one-size-fits-all framework. It is a customized program — and it’s important to understand an organization’s business objectives and critical flows, so that you can identify the best way to safeguard those objectives and flows.
Share with your network
Share